A computing security tool called Intel® Software Guard Extensions (Intel® SGX) creates a trusted execution environment (TEE) for users who require secure and private environments for things like private key management, multi-party computing with private data, and securing the deployment of critical applications to the public cloud.
These significant use cases are successfully addressed by the Intel® SGX SDK for Linux* OS, but its implementation is not straightforward. Because the OS is not trusted in the SGX SDK's threat model and only trusted applications and code can be worked on in the secure environment provided by SGX, i.e., a "enclave," it may necessitate significant system redesign and code changes by engineers. As a result, the trusted and untrusted components of the involved applications must be divided. Additionally, engineers will need to redesign some of their code base so that it can be trusted in this enclave. Finally, engineers may need to recompile SGX because of certain library dependencies that they may need to incorporate into the code base.
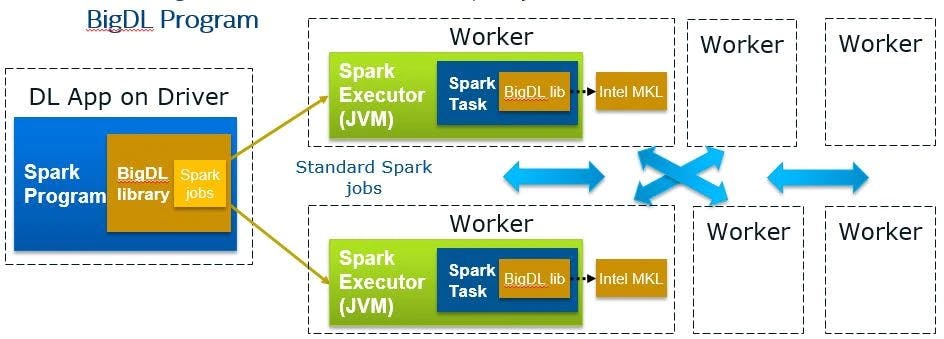
BigDL
In Intel's comprehensive developer portfolio of AI technologies, framework enhancements, and libraries, BigDL is included. It was created with the expanding demands of data scientists and data engineers in mind. BigDL gives data scientists and engineers access to features like DLlib, which offers simple access to a distributed deep learning library for Apache Spark, and Friesian, a sizable end-to-end recommender framework, among others, with a breadth that encompasses everything required for big end-to-end AI applications.
- Through its planned expansions, Ant Group will continue to highlight the significance of Occlum. Support for SGX EDMM (Enclave Dynamic Memory Management), which will allow much improved memory performance, is one forthcoming upgrade.
- They will also be able to further improve Occlumperformance *'s and stability thanks to support for Async/Await in Rust, which gives programmers the syntactic freedom to create non-blocking, asynchronous functions even when other parts of the code are still being executed synchronously due to a particularly long-running asynchronous task.
- Finally, Linux io uring, a kernel system call interface that Linux utilises to address some of the performance concerns of certain related asynchronous input/output operations using functions like read()/write, will be supported by Occlum* ()
Occulum*
Because Occlum is written in Rust, a programming language that prioritises memory safety, with several protections in place, such as avoidance of null pointers, dangling pointers, and data races, Occlum can maintain memory safety while maintaining this efficiency (a type of memory issue whereby two or more threads of a single process try to access that memory location simultaneously).
The applications and use cases that Occlum* supports are continuously being added to. BigDL PPML (Privacy Preserving Machine Learning), for instance, enables the expansion of a single node solution into a Trusted Cluster Environment, which is essential for handling analysis on enormous unmodified data sets and running many additional machine learning and deep learning applications.
Security is crucial in a world where data is everywhere and data is the backbone of AI and ML technologies. The ability to operate more effectively with big data and cutting-edge technology while maintaining safe coding standards would, in turn, be advantageous to every business in this field as well as to every individual, from managers to developers to product owners to end users.

